The purpose of the Heroku Application Publish task is to facilitate the publish an application to Heroku.
The process of configuration consists of two basic steps:
- Clone a source repository
- Push that repository to Heroku Git
Both of these steps may require additional access in order to read or write to the relevant repositories. In order to provide that access, Personal Access Tokens (PATs) are used to grant the build agent the access it needs to perform these actions.
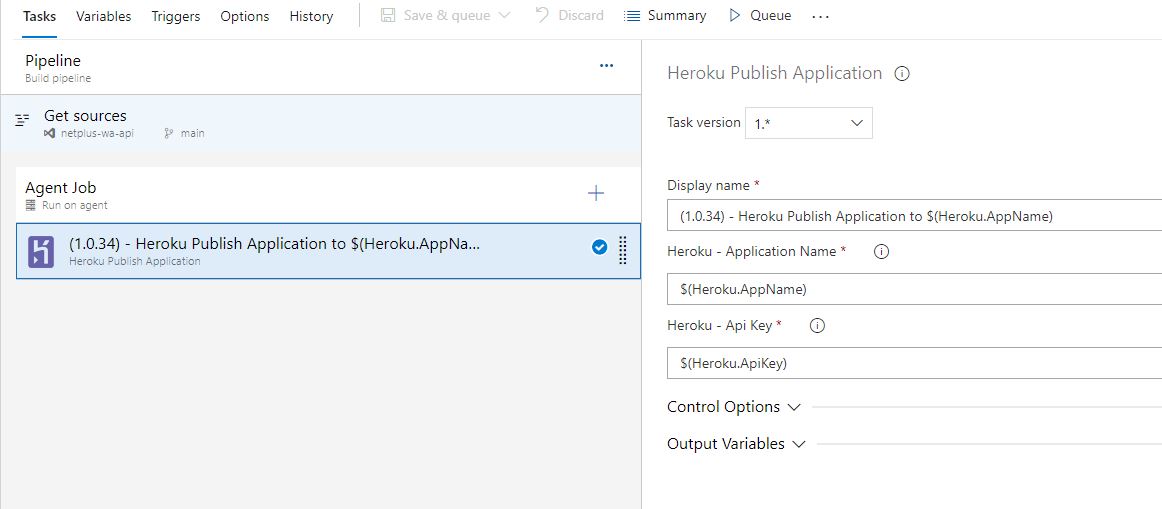
Heroku - Application Name
The application name
Heroku - Api Key
A Personal Access Token that grants read access to the Git repository. Is possible to obtain in a Account Settings in Heroku - https://dashboard.heroku.com/account
When using the Heroku Application Publish task in a YAML-based pipeline, the task configuration uses the following input names:
-
herokuApplicationName -
herokuApiKey -
There are still two fields that are not visible, which are the ones that get the current repository and the read access token from that repository.
- task: RenerLemes.netplus-vsextension-heroku.netplus-vsextension-heroku.netplus-vsextension-heroku@1
displayName: 'Heroku Publish Application'
inputs:
herokuApplicationName: 'heroku-app-name'
herokuApiKey: '123456-789012-345678-901234'In order to use this task, you will need to get the ApiKey. Below have a link on how to achieve this:
While you have the ability to enter the application name and api key into the task in plain-text, it is best practice to mask these values so that your repositories remain secure. Azure Pipelines supports the ability to manage and inject secure variables at build time. There are currently two ways to achieve this in Azure Pipelines:
By using secret variables in your build task, your values will be masked in any build output.
This extension was created based on vsts-mirror-git-repository, and much of the text and code was based on it.